Milad Aslaner
(Scariest session I’ve attended in a long time)
What is the background of social engineering? Con mans. Today, you just need a computer and you can be a con man. Social engineering is basically being a con man. They try to build trust, and then get to the next level.
There are key steps that hackers take before they start an attack.
Attack landscape has changed. Before hackers would try to attack the infrastructure to get secret data. Now, they just ask for the data. Phishing data emails
Attacker sends 100 emails, 23 will open it. 11 will open the attachment. 6 will do it in the fist hour.
Operation Stuxnet
Nuculear facility in Iran. They threw USB sticks into the parkinglot of the facility. People found them, and plugged them in. That is how the hackers got into that network.
Barium, Lead, Strongtium. All three are attack groups that leverage social media to attack various groups.
All of them leveraged social engineering.
Digitalization is happening everywhere. So you have to prepare and set security for these new digital endeavors. Information is the new currency. With information, you can rule the world. The weakest link is always the human.
Can’t rely solely on technology.
Human attacks:
- Its free
- Ignorance
- I have nothing of value
- Trust – I trust what I see.
Its not the user’s fault. The attacks are so complex, they can’t tell the difference between legitimate emails and phishing attacks.
Amount of data flowing is mind blowing!
Data Hunting
All kinds of data that we share is available. We freely give out info about ourselves. What we like. What we don’t like. Our favorite restaurants, foods, etc.

Hackers can leverage public data to guess passwords or challenge questions.
Hackers can use google.
Site:.gov intex:password filetype:xls
Maltigo. Tool can crawl many different data points for info. Start with one point of info, and see where it goes. He put in one person’s name, and found email, twitters, web sites. Etc. I can then find out what he is following, what he likes, etc. Using maltigo, you can see all kinds of data about a person and who they are. [this is freaking scary!]
Art of the attacks
Three types of attacks:
Human – putting pressure on someone. Emotion. For example, if you use the word “because”, people will do what you want. Triiger words.
Computer – exploits on machines. Like USB attack
Mobile – take a legitimate app, download, then modify and push it to another store.
- Starts with research.
- Target identification
- Establish trust
- Begin infiltration. Can be that day, or months or years later.
Social Engineering Toolkit – TrustedSec.
This tool automates the creation of hacker websites. It will clone websites. And then you can point phishers to it. It took 2 mins to create this.
So, what to do?
Threat Intelligence. Collects data on possible threats. Then they run analytics. Then leverage what they learn across the stack.
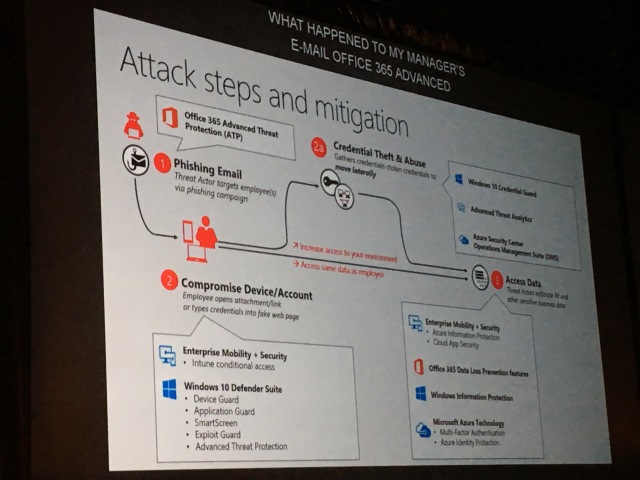
In addition to the products, they also use the Digital Crime Unit. Work to destroy bots.
All connects to the Microsoft stack.
Example:
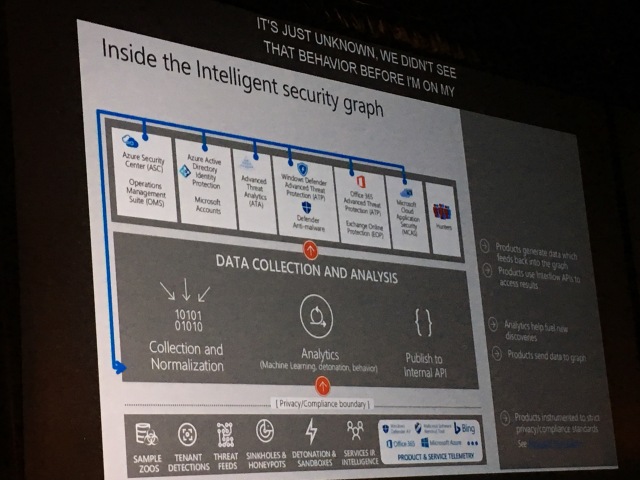
Windows Defender Security Center. – Sal – are you guys using this for Azure?


